-
Posts
15 -
Joined
-
Last visited
-
Days Won
5
Koorosh Sanaei Machinegun- last won the day on May 5
Koorosh Sanaei Machinegun- had the most liked content!
Recent Profile Visitors
The recent visitors block is disabled and is not being shown to other users.
Koorosh Sanaei Machinegun-'s Achievements
-
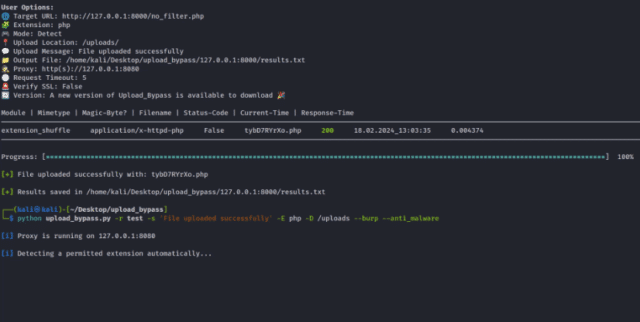
Upload_Bypass is a command-line tool that automates discovering and exploiting weak file upload filters. If you’re tired of manually renaming extensions and tweaking payloads by hand, this tool does the dirty work. File upload restrictions are one of the last lines of defence in many web apps and one of the most misunderstood. Some developers rely on MIME type checks. Others try to validate file extensions. A few go the extra mile with content inspection. But as any decent pentester knows, there’s almost always a way in. What Is Upload_Bypass? Upload_Bypass is a Python-based tool built by sAjibuu that helps bypass file upload protections commonly seen in CTFs, bug bounty targets, and poorly configured web apps. Instead of endlessly trying variations like shell.php, shell.php5, or shell.jpg.php, you can throw your file at Upload_Bypass and let it rip through automated filter evasion techniques, including: Filename and extension variations MIME type spoofing Header manipulation Extension appending (.jpg;.php) Uploading polyglot files (e.g. image + PHP) Why This Matters Improper file upload validation is one of the most common paths to remote code execution (RCE). Once you can smuggle a malicious file onto a server, you’ve got the ability to: Drop webshells Execute arbitrary code Establish persistence Escalate privilege (depending on misconfig) It’s one of the highest-ROI vulnerabilities in both offensive security and bug bounty hunting. Features Automatically tests multiple upload bypass payloads Supports common web extensions (.php, .asp, .jsp, .html) Smart payload renaming and MIME spoofing Verbose output to show what worked and what didn’t Designed for CTF players, bug bounty hunters, and red teamers Clean and hackable Python source Installation Simple setup on any system with Python 3: git clone https://github.com/sAjibuu/Upload_Bypass.git cd Upload_Bypass pip install -r requirements.txt python3 Upload_Bypass.py Example Usage Upload_Bypass is interactive. You’ll be prompted to: Select the file you want to upload Choose the output folder Pick target extension (e.g. .php) Specify the platform (web, mobile, ctf, etc.) Usage options: Usage: Upload Bypass [OPTIONS] Options: -h, --help Print help (see more with '--help') -U, --usage Print the how to save the request file instructions. -v, --version Print version Required Arguments: -r, --request_file <REQUEST_FILE> Provide a request file to be proccessed -E, --extension <EXTENSION> Forbidden extension to check (ex: php) -A, --allowed <EXTENSION> Allowed extension (ex: jpeg) - Optional - if not set the program will auto-detect the extension Choose only one from the options below: -s, --success <MESSAGE> Provide a success message when a file is uploaded (ex: File was uploaded successfully) -f, --failure <MESSAGE> Provide a failure message when a file is uploaded (ex: File is not allowed!) -S, --status_code <STATUS_CODE> Provide a status code for a success upload (ex: 200) Mode Settings: -d, --detect Upload harmless sample files (Suitable for a real penetration test) -e, --exploit Upload Web-Shells files when testing -a, --anti_malware Upload Anti-Malware Test file (Eicar) when testing I. If set with -E flag the program will test with the Eicar string along with the choosen extension II. If set without the -E flag the program will test with Eicar string and a com extension Modules Settings: -l, --list List all modules -i, --include_only <MODULES> Include only modules to test from (ex: extension_shuffle, double_extension) -x, --exclude <MODULES> Exclude modules (ex: svg_xxe, svg_xss) Request Settings: --base64 Encode the file data with Base64 algorithm --allow_redirects Follow redirects -P, --put Use the HTTP PUT method for the requests (Default is POST) -Pa, --patch Use the HTTP Patch method for the requests (Default is POST) -R, --response Print the response to the screen -c, --continue Continue testing all files, even if a few uploads encountered success -t, --time_out <NUM> Set the request timeout (Default is 8) -rl, --rate_limit <NUMBER> Set a rate-limit with a delay in milliseconds between each request Proxy Settings: -p, --proxy <PROXY> Proxy to use for requests (ex: http(s)://host:port, socks5(h)://host:port) -k, --insecure Do not verify SSL certificates --burp_http Set --proxy to 127.0.0.1:8080 and set --insecure to true (For HTTP requests) --burp_https Set --proxy to 127.0.0.1:8080 and set --insecure to false (For HTTPs requests) Optional Settings: -D, --upload_dir <UPLOAD_DIR> Provide a remote path where the Web-Shell should be uploaded (ex: /uploads) -o, --output <OUTPUT_PATH> Output file to write the results into - Default current directory (ex: ~/Desktop/results.txt) --debug <NUM> Debug mode - Print the stack trace error to the screen and save it to a file (ex: --debug 1) I. Level 1 - Saves only the stack trace error (default). II. Level 2 - Saves the stack trace error and user's arguments along with the request file. Resume settings: --resume <STATE_FILE> State file from which to resume a partially complete scan Update settings: -u, --update Update the program to the latest version The tool then generates a directory of modified versions of your original payload, each crafted to evade upload filters using different strategies. Test them manually or script uploads using Burp or cURL to see what slips past. Final Thoughts Upload_Bypass doesn’t promise magic—it doesn’t brute force login portals or drop zero-days. But it does exactly what it says: it it helps you bypass upload restrictions between you and shell access. If you’re tired of trying every bypass method manually, let Upload_Bypass do it for you—with better consistency and less risk of human error. Drop in your payload, choose your options, and go find the filter that fails. You can download Upload_Bypass or read more here: https://github.com/sAjibuu/Upload_Bypass
-
- 1
-

-
TELEGRAM @zirzamincybery0 SQLMap: SQLMap is an open-source tool that automates the process of detecting and exploiting SQL Injection vulnerabilities in web applications. It supports a wide range of databases and provides extensive options for both identification and exploitation. SQLNinja: SQLNinja is a tool specifically designed to exploit SQL Injection vulnerabilities in web applications that use Microsoft SQL Server as the backend database. It automates various stages of exploitation, including database fingerprinting and data extraction. JSQL Injection: A Java library focused on detecting SQL injection vulnerabilities within Java applications. It supports various types of SQL Injection attacks and provides a range of options for extracting data and taking control of the database. BBQSQL: BBQSQL is a Blind SQL Injection exploitation framework designed to be simple and highly effective for automated exploitation of Blind SQL Injection vulnerabilities.
-
AmiraliTelo started following Koorosh Sanaei Machinegun-
-
پست خوبی بود
-
BEST DDOS PANEL ⏩ Toxic 𝗡𝗲𝘁𝘄𝗼𝗿𝗸𝘀 | 𝗖𝟮/𝗔𝗣𝗜 𝗣𝗹𝗮𝗻𝘀 ⏪ ═══════════════════════════ 🔥𝗕asic 𝗣𝗹𝗮𝗻 🔥 (VIP: ❌) ⚡️𝟭 𝗖𝗼𝗻 | 𝟲𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 60 Sec Cooldown – $2𝟬/𝗠𝗼𝗻𝘁𝗵 💎Advanced 𝗣𝗹𝗮𝗻 💎 (VIP: ✅) ⚡️ 1 𝗖𝗼𝗻 | 𝟭𝟮𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 30 Sec Cooldown – $35/𝗠𝗼𝗻𝘁𝗵 👑 King 𝗣𝗹𝗮𝗻 👑 (VIP: ❌) ⚡️ 2 𝗖𝗼𝗻𝘀 | 𝟭6𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 30 Sec Cooldown – $6𝟬/𝗠𝗼𝗻𝘁𝗵 🚀 𝗣𝗥𝗘𝗠𝗜𝗨𝗠 𝗣𝗹𝗮𝗻 🚀 (VIP: ✅) ⚡️ 3 𝗖𝗼𝗻𝘀 | 𝟮𝟬𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 10 Sec Cooldown – $90/𝗠𝗼𝗻𝘁𝗵 ⚡️ Elite 𝗣𝗹𝗮𝗻 ⚡️ (VIP: ✅) ⚡️ 5 𝗖𝗼𝗻𝘀 | 𝟮𝟮𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 0 Sec Cooldown – $120/𝗠𝗼𝗻𝘁𝗵 ═══════════════════════════ ⏺ 𝗔𝗱𝗱𝗼𝗻𝘀 ⏺ 🗣 Home Holder 1 con, 86400 sec attack time - $20/month 🗣 Home Holder Extra con 1 - $15/month 🗣 VIP – $𝟭𝟱/𝗠𝗼𝗻𝘁𝗵 , $60/Lifetime 🗣 𝟭 𝗖𝗢𝗡 – $𝟭𝟱/𝗠𝗼𝗻𝘁𝗵 , $80/Lifetime 🗣 Botnet Access – $80/𝗠𝗼𝗻𝘁𝗵 🗣 Double Con – $20/𝗠𝗼𝗻𝘁𝗵 🗣 0 Cooldown – $15/𝗠𝗼𝗻𝘁𝗵 🗣 𝗘𝘅𝘁𝗿𝗮 𝟲𝟬 𝗦𝗲𝗰 – $𝟭𝟬/𝗠𝗼𝗻𝘁𝗵 , 40$/Lifetime 🗣 𝗔𝗣𝗜 𝗔𝗰𝗰𝗲𝘀𝘀 – $20/𝗠𝗼𝗻𝘁𝗵 , 120$/Lifetime ═══════════════════════════ 🛡 𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗧𝗼 𝗕𝘂𝘆 🛡 ➡️ [ @uz3er ] 💰 𝗣𝗮𝘆𝗺𝗲𝗻𝘁 𝗠𝗲𝘁𝗵𝗼𝗱𝘀: ══════════════════════════════ All Crypto: 💰 , 🔹 , 🪙 , 💲 , 💰 Other: DM Me For Other Payment ══════════════════════════════ • Toxicity Network Owned/Developed By @tox2c ⚡️ 📽️ TEST VIDEO برای خرید پلن دیداس و همچنین انجام تست به ایدی من در تلگرام پیغام بدید یا میتوانید به صورت مستقیم از وبسایت زیرزمین سایبری تهیه کنید : 😁: خرید از سایت به صورت مستقیم https://t.me/uz3er
-
چندین دورک جدید برای پیدا کردن دوربین در وبسایت SHODAN : دورک های محبوب پیدا کردن دوربین در Shodan "IP Camera" "HTTP/1.1 200 OK" Basic realm="IP Camera" admin/admin web camera Steven General camera search camera - 3,384,969 results Hikvision IP Cameras product:"Hikvision IP Camera" - 2,447,005 results Backdoor exploit at https://ipvm.com/reports/hik-exploit Webcams running on IPCam Client title:"IPCam Client" - 53,753 results Older webcams running on GeoVision server: GeoHttpServer - 34,111 results Vivotek IP cameras server: VVTK-HTTP-Server - 19,984 results Avigilion-brand camera/monitoring devices title:"Avigilon" - 17,181 results DVR CCTV cameras accessible via HTTP 200 ok dvr port:"81" - 6,287 results Netwave-make IP cameras Netwave IP Camera Content-Length: 2574 - 2,508 results A UK-based IP camera provider WWW-Authenticate: "Merit LILIN Ent. Co., Ltd" - 1,398 results Various IP camera/video management system products ACTi - 1,364 results UI3 - the HTML5 web interface for Blue Iris title:"ui3 -" - 875 results Yet another WebCAM software product:"Yawcam webcam viewer httpd" - 406 results Unsecured Linksys webcams title:"+tm01+" - 293 results Unsecured Linksys webcams Screenshot ContaCam Cameras title:"ContaCam" - 180 results Webcams running on webcamXP server: webcamxp - 141 results Webcams running on webcamXP Screenshot Webcams with screenshots webcam has_screenshot:true - 109 results Webcams running on webcam 7 server: "webcam 7" - 85 results Webcams running on webcam 7 Screenshot IP Webcams with screenshots has_screenshot:true IP Webcam - 43 results IP Webcams with screenshots Screenshot Canon-manufactured megapixel security cameras title:"Network Camera VB-M600" - 39 results i-Catcher IP-based CCTV systems server: "i-Catcher Console" - 27 results Linksys WVC80N cameras WVC80N - 19 results Webcams running on Blue Iris title:"blue iris remote view" - 16 results Industrial Control Systems EtherNet/IP port:44818 - 871,702 results S7 port:102 - 852,119 results BACnet port:47808 - 830,900 results Modbus port:502 - 791,691 results Niagara Fox port:1911,4911 product:Niagara - 7,943 results VNC Servers "authentication disabled" "RFB 003.008" - 5,607 results While not always 100% guaranteed to be a system, lots of embedded systems can show up here, along with personal systems. Gas Station Pump Controllers "in-tank inventory" port:10001 - 5,025 results Find gas station pump controllers with accessible inventory data. Gas Station Pump Controllers Screenshot Siemens Industrial Automation "Siemens, SIMATIC" port:161 - 2,760 results IEC 60870-5-104 port:2404 asdu address - 2,627 results DICOM Medical X-Ray Machines "DICOM Server Response" port:104 - 2,193 results More VNC Servers "authentication disabled" port:5900,5901 - 2,159 results Another search term for VNC servers - most are on port 5900 or 5901 as these are VNC display ports. Omron FINS port:9600 response code - 1,607 results DNP3 port:20000 source address - 1,364 results ProConOS port:20547 PLC - 706 results PCWorx port:1962 PLC - 703 results XZERES Wind Turbine title:"xzeres wind" - 263 results MELSEC-Q port:5006,5007 product:mitsubishi - 201 results Door / Lock Access Controllers "HID VertX" port:4070 - 139 results C4 Max Commercial Vehicle GPS Trackers [1m[35mWelcome on console - 32 results C4 Max Commercial Vehicle GPS Trackers Screenshot GaugeTech Electricity Meters "Server: EIG Embedded Web Server" "200 Document follows" - 29 results GaugeTech Electricity Meters Screenshot Open ATM NCR Port:"161" - 22 results Nordex Wind Turbine Farms http.title:"Nordex Control" "Windows 2000 5.0 x86" "Jetty/3.1 (JSP 1.1; Servlet 2.2; java 1.6.0_14)" - 19 results Voting Machines in the United States "voter system serial" country:US - 17 results Electric Vehicle Chargers "Server: gSOAP/2.8" "Content-Length: 583" - 16 results Traffic Light Controllers / Red Light Cameras mikrotik streetlight - 15 results Siemens HVAC Controllers "Server: Microsoft-WinCE" "Content-Length: 12581" - 6 results HART-IP port:5094 hart-ip - 6 results Fuel Pumps connected to internet "privileged command" GET - 5 results CAREL PlantVisor Refrigeration Units "Server: CarelDataServer" "200 Document follows" - 5 results CAREL PlantVisor Refrigeration Units Screenshot Samsung Electronic Billboards Server: Prismview Player - 3 results Search for electronic billboards managed by Prismview servers. Samsung Electronic Billboards Screenshot Railroad Management "log off" "select the appropriate" - 2 results Automatic License Plate Readers P372 "ANPR enabled" - 1 result Submarine Mission Control Dashboards title:"Slocum Fleet Mission Control" - 1 result Network Infastructure General MySQL Database Search product:MySQL - 2,903,663 results Remote PostgreSQL Connections port:5432 PostgreSQL - 600,520 results Default MongoDB Instances mongodb port:27017 - 68,492 results MongoDB Server Information on Default Port "MongoDB Server Information" port:27017 - 64,947 results Open Elasticsearch Databases port:"9200" all:elastic - 20,913 results Cisco Smart Install smart install client active - 6,294 results Listed Apache CouchDB product:"CouchDB" - 4,651 results Pi-hole Open DNS Servers "dnsmasq-pi-hole" "Recursion: enabled" - 2,854 results Android Root Bridges "Android Debug Bridge" "Device" port:5555 - 2,434 results Polycom Video Conferencing http.title:"- Polycom" "Server: lighttpd" - 2,174 results Jenkins CI "X-Jenkins" "Set-Cookie: JSESSIONID" http.title:"Dashboard" - 1,464 results Lantronix Serial-to-Ethernet Adapter Leaking Telnet Passwords Lantronix password port:30718 -secured - 494 results Already Logged-In as root via Telnet "root@" port:23 -login -password -name -Session - 359 results Accessible Kibana Dashboards kibana content-length:217 - 274 results Exposed MongoDB Express Web Interfaces "Set-Cookie: mongo-express=" "200 OK" - 261 results Docker Private Registries "Docker-Distribution-Api-Version: registry" "200 OK" -gitlab - 215 results Citrix Virtual Apps "Citrix Applications:" port:1604 - 152 results PBX IP Phone Gateways PBX "gateway console" -password port:23 - 135 results Telnet Configuration "Polycom Command Shell" -failed port:23 - 23 results Weave Scope Dashboards title:"Weave Scope" http.favicon.hash:567176827 - 10 results Vulnerable CouchDB Instances port:"5984"+Server: "CouchDB/2.1.0" - 2 results Printers General Printer Search printer - 92,694 results HP Printers Remote Restart port:161 hp - 8,692 results Canon Printer HTTP Servers Server: CANON HTTP Server - 6,380 results HTTP Accessible Epson Printers http 200 server epson -upnp - 1,301 results HTTP Accessible Epson Printers Screenshot Samsung Printers with SyncThru Web Service title:"syncthru web service" - 1,112 results Unsecured Telnet Access to Printers port:23 "Password is not set" - 319 results Remote Access to Xerox Printers ssl:"Xerox Generic Root" - 211 results Remote Access to Xerox Printers Screenshot Lexmark Printer Control Panels Printer Type: Lexmark - 141 results Epson Printers via HTTP Server "Server: EPSON-HTTP" "200 OK" - 120 results HP LaserJet Printers via HTTP "HP-ChaiSOE" port:"80" - 61 results Brother Printers Admin Interface "Location: /main/main.html" debut - 49 results Printers with FTP Access Laser Printer FTP Server - 20 results Exposed OctoPrint 3D Printer Controllers title:"OctoPrint" -title:"Login" http.favicon.hash:1307375944 - 17 results Files and Directories Open Lists of Files and Directories http.title:"Index of /" - 277,886 results Filezilla FTP filezilla port:"21" - 168,509 results Samba Shares with Authentication Disabled "Authentication: disabled" port:445 product:"Samba" - 113,230 results Open Lists on Port 80 port:80 title:"Index of /" - 98,587 results FTP Access Without Credentials "220" "230 Login successful." port:21 - 40,296 results Anonymous Access Allowed FTP "Anonymous access allowed" port:"21" - 21,892 results NDMP on FTP Port 10000 ftp port:"10000" - 7,503 results Vulnerable vsftpd Service vsftpd 2.3.4 - 1,705 results QuickBooks Files Shared Over Network "QuickBooks files OverNetwork" -unix port:445 - 23 results Compromised devices and websites Compromised Legacy Systems on Port 4444 port:4444 system32 - 1,111 results General Hacked Label Search hacked - 1,021 results Hacked By in HTTP Title http.title:"Hacked by" - 412 results Compromised Routers Labeled HACKED-ROUTER HACKED-ROUTER - 388 results Compromised Routers hacked-router-help-sos - 371 results Variation of Hacked By Label Search hacked by - 249 results Ransomware Infected RDP Services "attention" "encrypted" port:3389 - 47 results Compromised Hosts Advertising Default Password HACKED-ROUTER-HELP-SOS-HAD-DEFAULT-PASSWORD - 46 results Compromised FTP Servers HACKED FTP server - 23 results Bitcoin Ransomware with Screenshot bitcoin has_screenshot:true - 7 results Bitcoin Ransomware with Screenshot Screenshot Owned By Label in HTTP Title http.title:"0wn3d by" - 6 results Miscellaneous General Dashboard Interfaces http.title:"dashboard" - 354,607 results Control Panel Access Points http.title:"control panel" - 64,160 results Minecraft Servers "Minecraft Server" "protocol 340" port:25565 - 4,413 results Bitcoin Antminer Miners antminer - 1,659 results These devices are often left with default credentials. Bomgar Help Desk Portals "Server: Bomgar" "200 OK" - 354 results Tesla-related Interfaces http.title:"Tesla" - 346 results Everything in North Korea net:175.45.176.0/22,210.52.109.0/24,77.94.35.0/24 - 48 results EIG Electricity Meters "Server: EIG Embedded Web Server" "200 Document follows" - 29 results Misconfigured WordPress Installations http.html:"* The wp-config.php creation script uses this file" - 8 results Ethereum Miners ETH - Total speed - 2 results Telegram : @zirzamincybery0
-
Mahdi started following Koorosh Sanaei Machinegun-
-
Mr.Danial started following Koorosh Sanaei Machinegun-
-
https://t.me/cyber_punk_music
-
Tnx
-
itachi started following Koorosh Sanaei Machinegun-
-
🔴 چند روزی هستش که فروم BreachForums بالا نمیاد و شایعات مختلفی در اینترنت در حال پخشه. احتمال میدن که این فروم دوباره توسط FBI توقیف شده اما ThreatMon اعلام کرده که نشانه های رایج در خصوص توقیف توسط FBI وجود نداره. همچنین شایعاتی در خصوص دستگیری IntelBroker هم مطرح شده که فعلا مدرک یا تاییدی از سوی مراجع قانونی منتشر نشده. با این حال گروه هکری Dark Storm Team که خودش رو مدافع فلسطین میدونه و اخیرا حملاتی به پلتفرم X (https://t.me/onhex_ir/13229) انجام داده بود، اعلام کرده که برای سرگرمی این فروم رو زیر DDOS قرار داده. نکته جالب اینه که یک گروه تلگرامی که شایعه ی توقیف شدن این فروم توسط FBI رو پخش کرده بود، گفته یک دامنه ی جدید برای این فروم ثبت شده اما برای دسترسی نیاز به پرداخت 250 دلار بصورت XMR هستش که مشخص شده کلاهبرداری هستش. این فرم بعد از دستگیری (https://t.me/onhex_ir/11710) مالکش، Pompompurin، دوباره توسط نفر دوم فروم، Blaphomet دوباره بالا اومد. اما دوباره توسط FBI توقیف (https://t.me/onhex_ir/12658) شد. نسخه ی سوم این فروم توسط Shiny Hunters و USDoD دوباره بالا (https://t.me/onhex_ir/12674) اومد. اعلام شده که Shiny در روزهای اخیر تلگرام خودش رو حذف کرده. گروه Dark Storm هم که یک گروه هکتویست طرفدار فلسطین هستش عمدتا روی تخریب زیرساختهای اسرائیل تمرکز داره و از سال 2023 در تلگرم فعالیت میکنه. فعالیت این گروه مشابه گروه Killnet هستش که در سال 2023 حامیان اوکراین رو DDOS میکرد و بعدش خدماتش رو بصورت DDoS hackers-for-hire تجاری کرد. بر اساس گزارش (https://securityscorecard.com/research/hacktivist-involvement-in-israel-hamas-war-reflects-possible-shift-in-threat-actor-focus/) اطلاعات ریسک سایبری SecurityScorecard از سال ۲۰۲۳، گروه Dark Storm نه تنها دولت اسرائیل، شهرداریهای محلی و صنایع حساس رو هدف قرار داده، بلکه ادعای حملات DDoS به فرودگاه جان اف. کندی در نیویورک، فرودگاه لسآنجلس (LAX) و اسنپچت رو هم کرده. بعد از حمله این گروه به X، یک محقق امنیتی فرانسوی به نام Baptiste Robert، مدیرعامل Predicta Labs، ادعا کرد که هویت هکر Dark Storm رو کشف کرده. (https://www.predictagraph.com/graph/snapshot/93bd7e60-2d6f-4c4e-8562-36ade22db0e3) یک دانشجوی مهندسی حدود ۲۰ ساله از مصر./منبع (https://cybernews.com/news/breachforums-dark-storm-ddos-cyberattack-fbi-hackers/)
-
لینک مشاهده آموزش اگر علاقه مند به آموزش کرک VPS هستید از اینجا شروع کنید . :
-
Koorosh Sanaei Machinegun- changed their profile photo
-
Koorosh Sanaei Machinegun- started following Hello UnderGroundCY ! and Toxic 𝗡𝗲𝘁𝘄𝗼𝗿𝗸𝘀 | 𝗖𝟮/𝗔𝗣𝗜 𝗣𝗹𝗮𝗻𝘀
-
⏩ Toxic 𝗡𝗲𝘁𝘄𝗼𝗿𝗸𝘀 | 𝗖𝟮/𝗔𝗣𝗜 𝗣𝗹𝗮𝗻𝘀 ⏪ ═══════════════════════════ 🔥𝗕asic 𝗣𝗹𝗮𝗻 🔥 (VIP: ❌) ⚡️𝟭 𝗖𝗼𝗻 | 𝟲𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 60 Sec Cooldown – $2𝟬/𝗠𝗼𝗻𝘁𝗵 💎Advanced 𝗣𝗹𝗮𝗻 💎 (VIP: ✅) ⚡️ 1 𝗖𝗼𝗻 | 𝟭𝟮𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 30 Sec Cooldown – $35/𝗠𝗼𝗻𝘁𝗵 👑 King 𝗣𝗹𝗮𝗻 👑 (VIP: ❌) ⚡️ 2 𝗖𝗼𝗻𝘀 | 𝟭6𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 30 Sec Cooldown – $6𝟬/𝗠𝗼𝗻𝘁𝗵 🚀 𝗣𝗥𝗘𝗠𝗜𝗨𝗠 𝗣𝗹𝗮𝗻 🚀 (VIP: ✅) ⚡️ 3 𝗖𝗼𝗻𝘀 | 𝟮𝟬𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 10 Sec Cooldown – $90/𝗠𝗼𝗻𝘁𝗵 ⚡️ Elite 𝗣𝗹𝗮𝗻 ⚡️ (VIP: ✅) ⚡️ 5 𝗖𝗼𝗻𝘀 | 𝟮𝟮𝟬 𝘀𝗲𝗰𝗼𝗻𝗱𝘀 | 0 Sec Cooldown – $120/𝗠𝗼𝗻𝘁𝗵 ═══════════════════════════ ⏺ 𝗔𝗱𝗱𝗼𝗻𝘀 ⏺ 🗣 Home Holder 1 con, 86400 sec attack time - $20/month 🗣 Home Holder Extra con 1 - $15/month 🗣 VIP – $𝟭𝟱/𝗠𝗼𝗻𝘁𝗵 , $60/Lifetime 🗣 𝟭 𝗖𝗢𝗡 – $𝟭𝟱/𝗠𝗼𝗻𝘁𝗵 , $80/Lifetime 🗣 Botnet Access – $80/𝗠𝗼𝗻𝘁𝗵 🗣 Double Con – $20/𝗠𝗼𝗻𝘁𝗵 🗣 0 Cooldown – $15/𝗠𝗼𝗻𝘁𝗵 🗣 𝗘𝘅𝘁𝗿𝗮 𝟲𝟬 𝗦𝗲𝗰 – $𝟭𝟬/𝗠𝗼𝗻𝘁𝗵 , 40$/Lifetime 🗣 𝗔𝗣𝗜 𝗔𝗰𝗰𝗲𝘀𝘀 – $20/𝗠𝗼𝗻𝘁𝗵 , 120$/Lifetime ═══════════════════════════ 🛡 𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗧𝗼 𝗕𝘂𝘆 🛡 ➡️ [ @uz3er ] 💰 𝗣𝗮𝘆𝗺𝗲𝗻𝘁 𝗠𝗲𝘁𝗵𝗼𝗱𝘀: ══════════════════════════════ All Crypto: 💰 , 🔹 , 🪙 , 💲 , 💰 Other: DM Me For Other Payment ══════════════════════════════ • Toxicity Network Owned/Developed By @tox2c ⚡️ 📽️ TEST VIDEO برای خرید پلن دیداس و همچنین انجام تست به ایدی من در تلگرام پیغام بدید یا میتوانید به صورت مستقیم از وبسایت زیرزمین سایبری تهیه کنید : 😁: خرید از سایت به صورت مستقیم https://t.me/uz3er
- 1 reply
-
- 2
-

-

-
- 1 reply
-
- 3
-

-